Introduction
Recently I came up with a new idea, I usually revert back to my lazy self on weekends, sleeping long and doing pretty much nothing productive at all, which is a lot of wasted time. So I challenged myself to acquire one new skill each weekend in May, see how it goes and maybe extend this into June.
Anyway, for this weekend I am trying to get a basic knowledge of penetration-testing.
What is penetration-testing?
Roughly said, it is using a set of tools and trying to break into an IT system. But there is a lot more to that, a lot of knowledge needed to be able to use these tools.
Some of you might want to know why I am doing this, no need to worry, I am not planning on hacking anyone, but getting into this and understanding how these things are done also leads to a deeper understanding on how to secure a server against these exploits, what to look for and that would be something I am doing on my job. I am also not going to go an put a step by step guide here on how to get into a web server, as this would probably get some kids into trouble….
Getting started
For this little project I am going to need three things.
A.) Base knowledge of how to go about this
B.) A Set of tools that enables me to test the base knowledge
C.) A target
Let’s go about this step by step. Base knowledge, I do already know a bit about IT-security so I have a basis to build on. I am going to go with what I already know and proceed from there. But maybe I am going to learn that I know pretty much nothing at all.
So here is what I think I know
If an attacker is able to get into a system it usually means someone along the way made a mistake. These mistakes could be embedded in the hardware, for example Intels MDS flaws. There are also those embedded in the operating system or an application. There are specific sites that list all the know vulnerabilities of OSes so I am not going to get into this right now. What about applications. One application that comes to mind is open ssl, which suffered from a bug recently that became known as heartbleed. Another mistake is having users on computers. All that security sysadmins are building up can easily be bypassed by weak passwords or by simply sending an email with certain attachments. Last: improper usage of software. A badly setup Apache server for example or running a CMS and not updating it come to mind. I am going to go with the assumption here, that most successful attacks are done via the last two vectors.
The set of tools
Having some friends that actually make a living on these things and also spending way to much time on Linux an security channels I heard about Kali Linux. It is a Linux distribution that comes with a pre-installed set of tools usually used to perform these tests. I went ahead and installed in within a VM,
The target
Obviously I am not going to try an get into someones systems, normally one would set up a second vm, but some stuff on it and try attacking it. But where is the fun in being normal? I have a NextCloud server at home that I use on a daily basis, it is accessible from the internet and going to be one of my targets for today. That one is the snap version of NextCloud. Snaps have an immutable part and a writable part. All php files etc are within the immutable part only the user data part is writable so I am going to predict there is a slimmer chance for access. The second target is also a webserver, one I did a manual install of NextCloud on and haven’t booted for some time, so updates are missing. Also I haven’t put much effort in the installation, just put the files on there and left everything on defaults, as it was only an internal test of the new version of NextCloud. I’d say there should be a vulnerability. I will target both servers from outside my firewall and from within the network. My firewall has an intrusion prevention system that should detect attack patterns and drop those prior to reaching my webservers, but who knows.
Expectation
I have literally zero experience in performing pen-tests and I am basing every step on online research and the kali Linux reveled book to be found here: https://kali.training/downloads/Kali-Linux-Revealed-1st-edition.pdf
Knowing that I know nothing about this is important, because if I can’t get in it doesn’t mean my system is secure and if I can get in, security really sucks.
What I am expecting to see is the following: I won’t get into the productive NC server neither from the inside nor the outside. But I will breach the test server, as I deliberately used weak passwords, have many open ports and only use standard ports for all applications. That is I will do that from the inside. I will not test it against the firewall from the outside, I am not willing to make such an insecure server accessible from the internet. But I can get the attacker outside the firewall with some creative routing.
Starting the experiment
Let’s assume the only thing I know so far about my target is the domain name. That name is home.companyname.com. That doesn’t really tell me much since this could be anything from a remote machine to a web server.
In order to find out what I am dealing with I am using nmap, a port scanning application to find out which ports are open.
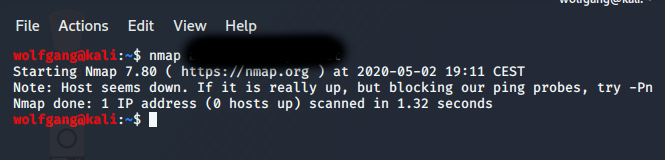
Now that did not tell me much. But it is giving us a hint, -Pn a quick look into the manual states: treat all hosts as online. Running that command actually reveled an open port, not the one I was targeting and it is fixed now, but as you can see even playing with these basic things might already reveal something. Anyway, the second attack vector is someone gained access to the network behind the firewall, running nmap on the networks range revealed all servers and open ports and OS + version. which would really help.
But I am going to assume the evil attacker actually found the correct port and came to the conclusion of it being a web server. According to some forums nikto is a good next step, so I am firing that against my domain.
That program should list a little information on the target. Meanwhile I am running dirbuster against the machine as well. Looking at various logs I can see that my firewall is actually fighting against these probes, but a couple of request go through which I can see on my Nextclouds logs, i.e. the attacker is trying to brute force its way in using various common usernames and passwords (i.e. admin and P@ssw0rd, don’t do that…)
Also these tools seem to be probing common directories such as myadmin for those PHP-MyAdmin fans out there.
What are we seeing here? Mostly these tests take a long time, I choose a medium list of attacks and it took 2 hours for the list to be done. But also that there is a long long list of mistakes that are commonly made in setting up a webserver, many are widely know and automatically fired against the server.
Conclusion
First up, there is no way anyone can get deeply into penetration testing within one day, I read so many guides to kali and watched oh so many videos my eyes are hurting by now, but it is a highly interesting field.
Also while being time consuming it is not really hard to get into, there are tools you just need to use to get a list of vulnerabilities on your target. Provided by people who seem to know what they are doing. Some are even GUI tools, so no hollywood hacker feeling…
Oh also, the Snap Nextcloud did very well, but I don’t want to talk about my own install, that did not shine…
I rerouted my servers connections so Kali could only access it behind the firewall at last, results where much better, intrusion prevention systems do make sense and balance out a bad webadmin to some degree.
Use two-factor if possible, but at least use secure passwords and usernames, here is a list of some that are tried by default:
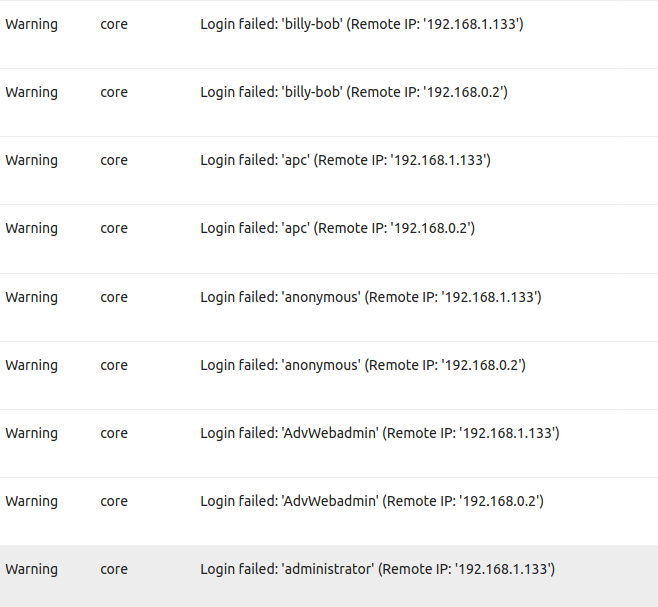
As you can see the attacking IP changed, that was intentional, so I would not trigger any mechanism that block IPs that access to often, even that was rather easy to accomplish using VPNs.
I think for a first try I did not do to badly but I did not get in. As I said, that means nothing, because there is very likely a bad vulnerability somewhere, I am just not able to find it as I lack a lot of knowledge.
Also it was really fun learning all this stuff, some of the probes I did expect, others where in the “what the hell, why did I never bother with that” department. While I failed to become the worlds greatest hacker in one day (which was expected) I managed to learn how basic attacks are carried out and what to look for on servers to prevent them from being successful. I think, I will keep this up, explore a little further, gain more insight….
